Round Key Generation In Aes Example
I want to use encryption algorithm available in.Net Security namespace, however I am trying to understand how to generate the key, for example AES algorithm needs 256 bits, that 16 bytes key, and some initialization vector, which is also few bytes. Can I use any combination of values in my Key and IV? All zeros in Key and IV are valid or not? Jan 10, 2018 AES algorithm is the Block Cipher Symmetric Algorithm Block Size is 128 bits Key Size is 128 bits ( 4 words or 16 Bytes ) Sub Key Size is 1 Word (32 bit) Number of Sub keys 44 Words Number of. Key Generation. The round-key generator creates sixteen 48-bit keys out of a 56-bit cipher key. The process of key generation is depicted in the following illustration − The logic for Parity drop, shifting, and Compression P-box is given in the DES description. DES Analysis. The DES satisfies both the desired properties of block cipher.
Finally, bitaddress uses accumulated entropy to generate a private key. It needs to generate 32 bytes. For this task, bitaddress uses an RNG algorithm called ARC4. The program initializes ARC4 with the current time and collected entropy, then gets bytes one by one 32 times. I am having trouble generating a private key. My main problem is understanding the relation of my equations to each other. To set everything up, we have. The implementation of the Extended Euclidean algorithm you have is not complete, since it is generating a negative number for the private key. Algorithms for generating private key. Generating Symmetric Private Key In C# and.NET. Generating Symmetric Private Key In C# and.NET. Major symmetric algorithms are AES, DES, RC2, Rijndael, and TripleDES. The GenerateKey and GenerateIV methods return the private secret key and initialization vector. Because of this, a public key can be freely shared. The private key however belongs to only one person. There are several well-known mathematical algorithms that are used to produce the public and private key. Some well-respected examples of public private key encryption are RSA, DSS (Digital Signature Standard) and various elliptic curve techniques. Mar 03, 2020 The device uses a private key to sign a JSON Web Token (JWT). The token is passed to Cloud IoT Core as proof of the device's identity. The service uses the device public key.
AES uses a key schedule to expand a short key into a number of separate round keys. The three AES variants have a different number of rounds. Each variant requires a separate 128-bit round key for each round plus one more.[note 1] The key schedule produces the needed round keys from the initial key.
Steps in the AES Encryption Process. But first we need to look in more detail at the generation of the Round Keys, so called because there is a different one for each round in the process. Of the corresponding word in the previous round key and the preceding word in the current round key. For example, using XOR for addition: 1 Using.
Round constants[edit]
| i | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 |
|---|---|---|---|---|---|---|---|---|---|---|
| rci | 01 | 02 | 04 | 08 | 10 | 20 | 40 | 80 | 1B | 36 |
The round constant rconi for round i of the key expansion is the 32-bit word:
where rci is an eight-bit value defined as:
where is the bitwise XOR operator and constants such as 0016 and 1B16 are given in hexadecimal. Equivalently:
where the bits of rci are treated as the coefficients of an element of the finite field, so that e.g. represents the polynomial .
AES uses up to rcon10 for AES-128 (as 11 round keys are needed), up to rcon8 for AES-192, and up to rcon7 for AES-256.[note 2]
The key schedule[edit]
Define:
- N as the length of the key in 32-bit words: 4 words for AES-128, 6 words for AES-192, and 8 words for AES-256
- K0, K1, .. KN-1 as the 32-bit words of the original key
- R as the number of round keys needed: 11 round keys for AES-128, 13 keys for AES-192, and 15 keys for AES-256[note 3]
- W0, W1, .. W4R-1 as the 32-bit words of the expanded key[note 4]
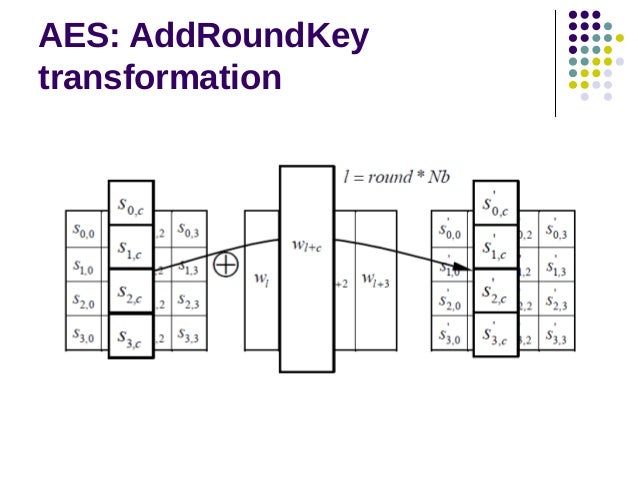
Aes Round Key
Also define RotWord as a one-byte left circular shift:
and SubWord as an application of the AES S-box to each of the four bytes of the word:
Round Key Generation In Aes Examples
Then for :
Jan 31, 2020 Adobe Photoshop CS5 Full Version MAC + Windows. Adobe Photoshop CS5 Crack is one of the remarkable program for the professional image editing and graphics designing. There are thousands of the tools and features are available in this stunning program that helps the. Adobe photoshop cs5 keygen free download - Adobe Photoshop CC, Adobe Photoshop CS5 Extended trial, Adobe Fireworks CS5, and many more programs. Adobe photoshop cs5 key generator free download windows 7.
Notes[edit]
- ^Non-AES Rijndael variants require up to 256 bits of expanded key per round
- ^The Rijndael variants with larger block sizes use more of these constants, up to rcon29 for Rijndael with 128-bit keys and 256 bit blocks (needs 15 round keys of each 256 bit, which means 30 full rounds of key expansion, which means 29 calls to the key schedule core using the round constants). The remaining constants for i ≥ 11 are: 6C, D8, AB, 4D, 9A, 2F, 5E, BC, 63, C6, 97, 35, 6A, D4, B3, 7D, FA, EF and C5
- ^Other Rijndael variants require max(N, B) + 7 round keys, where B is the block size in words
- ^Other Rijndael variants require BR words of expanded key, where B is the block size in words
References[edit]
- FIPS PUB 197: the official AES standard (PDF file)
External links[edit]
- schematic view of the key schedule for 128 and 256 bit keysfor 160-bit keys on Cryptography Stack Exchange