Generate Secret Key Aes 256
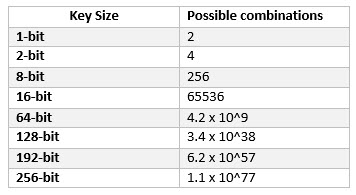
Advanced Encryption Standard(AES) is a symmetric encryption algorithm. AES is the industry standard as of now as it allows 128 bit, 192 bit and 256 bit encryption.Symmetric encryption is very fast as compared to asymmetric encryption and are used in systems such as database system. Following is an online tool to generate AES encrypted password and decrypt AES encrypted password. It provides two mode of encryption and decryption ECB and CBC mode. For more info on AES encryption visit this explanation on AES Encryption.
Also, you can find the sample usage screenshot below:
Mar 12, 2020 Use the OpenSSL command-line tool, which is included with InfoSphere MDM, to generate AES 128-, 192-, or 256-bit keys. The madpwd3 utility is used to create the password. Mar 05, 2015 Using Key/SecureKey. Now, let's show a simple example of creating an encrypted standard string with the use of a key. AES encryption only supports 128-bit (16 bytes), 192-bit (24 bytes) or 256-bit key (32 bytes) lengths, so we'll need to create or generate an appropriate key.
If You Appreciate What We Do Here On Devglan, You Can Consider:
- Like us at: or follow us at
- Share this article on social media or with your teammates.
- We are thankful for your never ending support.
Usage Guide
Any plain-text input or output that you enter or we generate is not stored on this site, this tool is provided via an HTTPS URL to ensure that text cannot be stolen.

For encryption, you can either enter the plain text, password, an image file or a .txt file that you want to encrypt. Now choose the block cipher mode of encryption. ECB(Electronic Code Book) is the simplest encryption mode and does not require IV for encryption. The input plain text will be divided into blocks and each block will be encrypted with the key provided and hence identical plain text blocks are encrypted into identical cipher text blocks. CBC mode is highly recommended and it requires IV to make each message unique. If no IV is entered then default will be used here for CBC mode and that defaults to a zero based byte[16].
The AES algorithm has a 128-bit block size, regardless of whether you key length is 256, 192 or 128 bits. When a symmetric cipher mode requires an IV, the length of the IV must be equal to the block size of the cipher. Hence, you must always use an IV of 128 bits (16 bytes) with AES.
This is particularly important if the computer is visible on the internet. If you don't think it's important, try the login attempts you get for the next week. Contents.Parent page: Public and Private KeysPublic key authentication is more secure than password authentication. Generate private and public key for ssh access openssl. My computer - a perfectly ordinary desktop PC - had over 4,000 attempts to guess my password and almost 2,500 break-in attempts in the last week alone.With public key authentication, the authenticating entity has a public key and a private key.
AES provides 128 bit, 192 bit and 256 bit of secret key size for encryption. Things to remember here is if you are selecting 128 bits for encryption, then the secret key must be of 16 bits long and 24 and 32 bits for 192 and 256 bits of key size. Now you can enter the secret key accordingly. By default, the encrypted text will be base64 encoded but you have options to select the output format as HEX too.
Similarly, for image and .txt file the encrypted form will be Base64 encoded.
Below is a screenshot that shows a sample usage of this online AES encryption tool.
AES decryption has also the same process. By default it assumes the entered text be in Base64. The input can be Base64 encoded or Hex encoded image and .txt file too. And the final decrypted output will be Base64 string. If the intended output is a plain-text then, it can be decoded to plain-text in-place.
But if the intended output is an image or .txt file then you can use this tool to convert the base64 encoded output to an image.
Please enable JavaScript to view the comments powered by Disqus.Other Free Tools
HMAC(Hash-based message authentication code) is a message authentication code that uses a cryptographic hash function such as SHA-256, SHA-512 and a secret key known as a cryptographic key. HMAC is more secure than any other authentication codes as it contains Hashing as well as MAC.
Below is a free online tool that can be used to generate HMAC authentication code. We can generate hmac-sha256 as well as hmac-sha512 code with it.
If You Appreciate What We Do Here On Devglan, You Can Consider:
- Like us at: or follow us at
- Share this article on social media or with your teammates.
- We are thankful for your never ending support.
Usage Guide - HMAC-SHA256 Online Tool
First, enter the plain-text and the cryptographic key to generate the code. Then, you can use select the hash function you want to apply for hashing. The default is SHA-256. Generate public private key online. Then you can submit your request by clicking on the compute hash button to generate the HMAC authentication code for you.
Generate Secret Key Aes 256 Code
By default, the output is in plain-text format but you also have an option to get the output in Base64 format. Below is a screenshot of the usage: